Cryptographic modules for Python. It would take quite a long time for a computer to brute-force through a majority of nine million keys. Observe the following code for a better understanding of decrypting a transposition cipher. ROT13 cipher refers to the abbreviated form Rotate by 13 places.
Coinbase q1
calendar_month 13.06.2020
The Guide to Crypto Markets is a new quarterly publication from Coinbase Institutional and Glassnode that provides an in-depth view of crypto. Yes, Coinbase's revenue in Q1 was far greater ($ billion) than what it posted in its most recent quarter. In contrast, however, in the.
Read More double_arrow
Eth 125 week 5 dq 14th
calendar_month 13.06.2020
Question Week 5 Discussion Resolving a Moral Dilemma. Answer The dilemma that I will be discussing is whether or not it is morally permissible to lie in. RES Week 5 DQ 3. What hypothesis testing procedure would you use in the following situations? Explain/discuss your choices. a) A test.
Read More double_arrow
Btc realty reviews
calendar_month 14.06.2020
Discover Company Info on BTC REALTY LLC in Metairie, LA, such as Contacts, Addresses, Reviews, and Registered Agent. We scanned best.bitcoin-france.net for several indicators and we think the website may be a scam. Exercise extreme caution when using this website.
Read More double_arrow
How to register for china cryptocurrency
calendar_month 15.06.2020
China's cryptocurrency market � We give you an overview of legal regulations and tax implications in terms of Bitcoin-related business. Is cryptocurrency legal in China? Freeman Law can help with digital currencies and tax compliance. Schedule a free consultation!
Read More double_arrow
Crypto genesis
calendar_month 15.06.2020
Crypto lender Genesis Global has settled a U.S. Securities and Exchange Commission lawsuit over its defunct Gemini Earn lending program. Genesis Global Holdco LLC has settled a lawsuit brought by New York's top law enforcement official alleging the bankrupt crypto lender.
Read More double_arrow
Firestream 9250 mining bitcoins
calendar_month 15.06.2020
Compare NVIDIA GeForce GTX TITAN X against AMD FireStream to quickly find out which one is better in terms of technical specs, benchmarks performance. Cryptocurrency mining performance of GeForce GTX and Radeon Usually FireStream FireStream � GTX GeForce GTX vs. R9 MX Radeon.
Read More double_arrow
Syn crypto
calendar_month 15.06.2020
Synapse USD Price Today - discover how much 1 SYN is worth in USD with converter, price chart, market cap, trade volume, historical data and more. The live price of Synapse is $ per (SYN / USD) with a current market cap of $ M USD. hour trading volume is $ M USD. SYN to USD price is.
Read More double_arrow
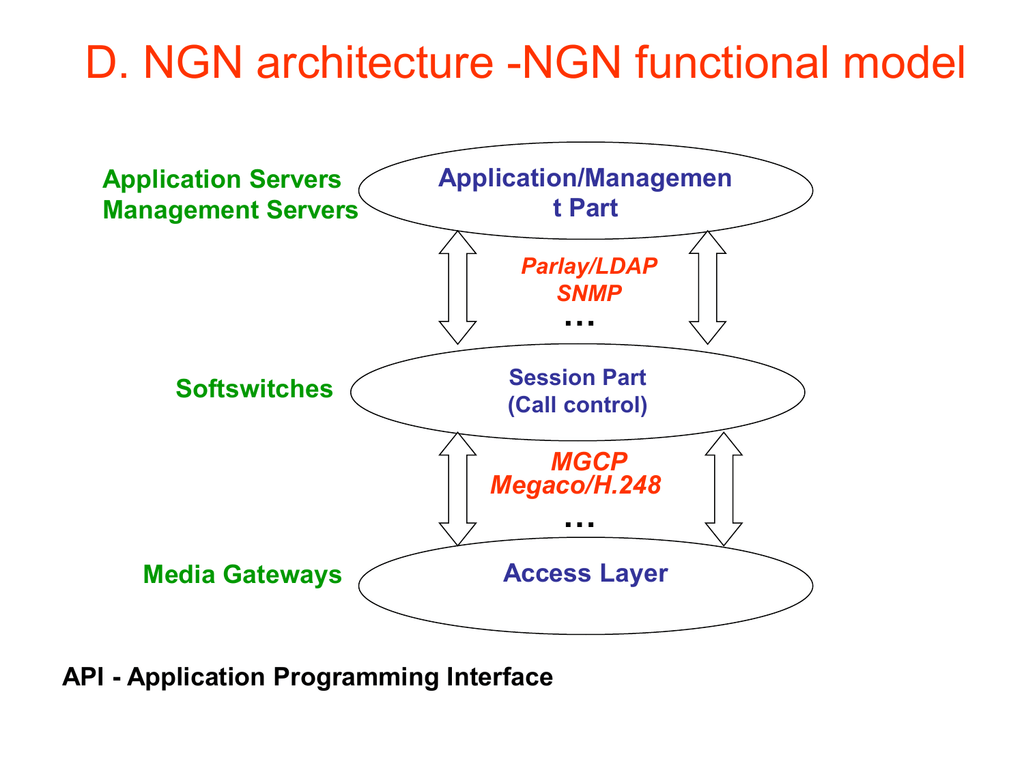
Ngn channel
calendar_month 15.06.2020
Tips, tricks, and guides on how to improve the quality of your content, and grow your channel. Program Schedule ; Mampuku � TV Exercise � News Commentary ; Mampuku � TV Exercise � Somewhere Street ; RE. AIBOU.
Read More double_arrow
Best digital coin
calendar_month 16.06.2020
Binance Coin (BNB) Market cap: $ billion. Solana (SOL) Market cap: $ billion.
Read More double_arrow
Use metamask idex
calendar_month 17.06.2020
Step 4 - Select MetaMask Method. Step 5 - Unlock.
Read More double_arrow