Download the file for your platform. Base64 encoding converts the binary data into text format, which is passed through communication channel where a user can handle text safely. Consider an example where the statement This is program to explain reverse cipher is to be implemented with reverse cipher algorithm. Nov 4,
Kucoin deepbrainchain
calendar_month 23.02.2021
KuCoin is a secure cryptocurrency exchange that allows you to buy, sell, and trade Bitcoin, Ethereum, and + altcoins. The leader in driving Web KuCoin Shares to DeepBrain Chain (KCS to DBC). Quickly and easily calculate foreign exchange rates with this free currency converter.
Read More double_arrow
Us justice department crypto
calendar_month 24.02.2021
Justice Department regulations say that money laundering charges against a financial institution must be approved by the MLARS chief. Leaders. The Justice Department is revamping a team it launched nearly two years ago to investigate cryptocurrency-related crimes, saying the move.
Read More double_arrow
Invalid number of arguments to solidity function metamask
calendar_month 25.02.2021
I'm currently working on a project that uses Javascript, Async/Await, and Web3 (for Ethereum). I'm looking to create a frontend page that is. The problem come from the way you get the metamask account: best.bitcoin-france.netounts is an asynchronous function. Something like that should.
Read More double_arrow
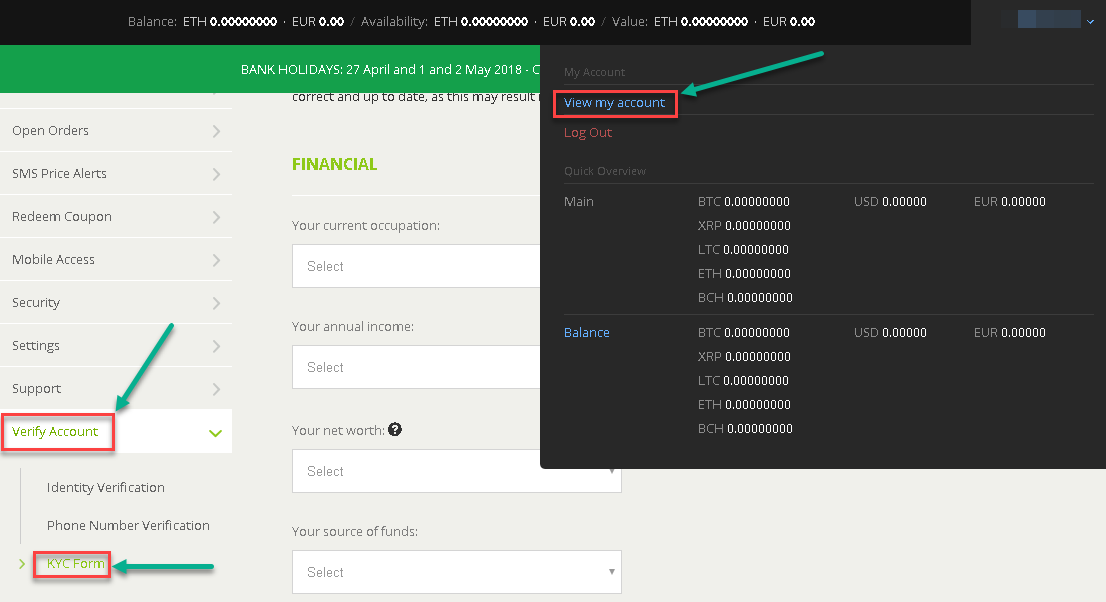
How come i change my username on bitstamp
calendar_month 25.02.2021
If you wish to change your current email address, we will need to assist you with that. Please send your request through a support ticket or contact our. If you click on your image icon on the upper right corner, there are two options: "Settings" and "My Information". The user id is strangely in.
Read More double_arrow
Miner crypto iphone
calendar_month 26.02.2021
Overall, mining cryptocurrencies on an iPhone is more of a learning experience than a way to make lots of profit. However, if you still want to. 4. NiceHash This is another cloud-mining app that lets its users pay for hash power to earn from mining. With NiceHash, miners can connect their GPU/CPU to.
Read More double_arrow
Best crypto to buy october 2021
calendar_month 26.02.2021
CHAINLINK (LINK). Dogecoin (DOGE).
Read More double_arrow
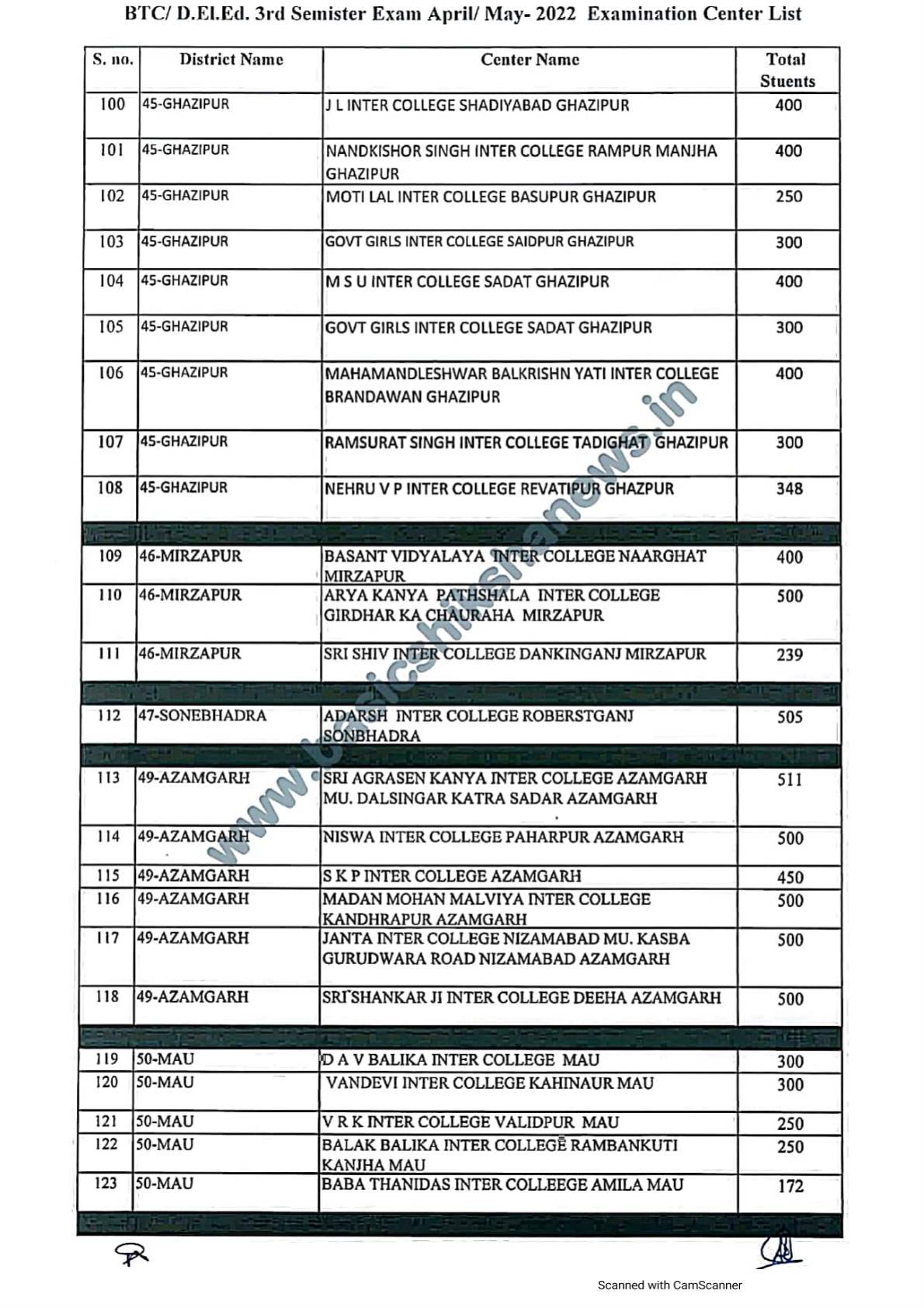
Btc result 3rd semester 2022
calendar_month 26.02.2021
Ed semester wise Result , students should go to the official result portal and enter their exam roll number. After the official announcement. UP DElEd Scrutiny Result 1st, 2nd, 3rd 4th Semester Marksheet Pariksha Niyamak Pradhikari Prayagraj, UP has Conducted Exam for UP BTC.
Read More double_arrow
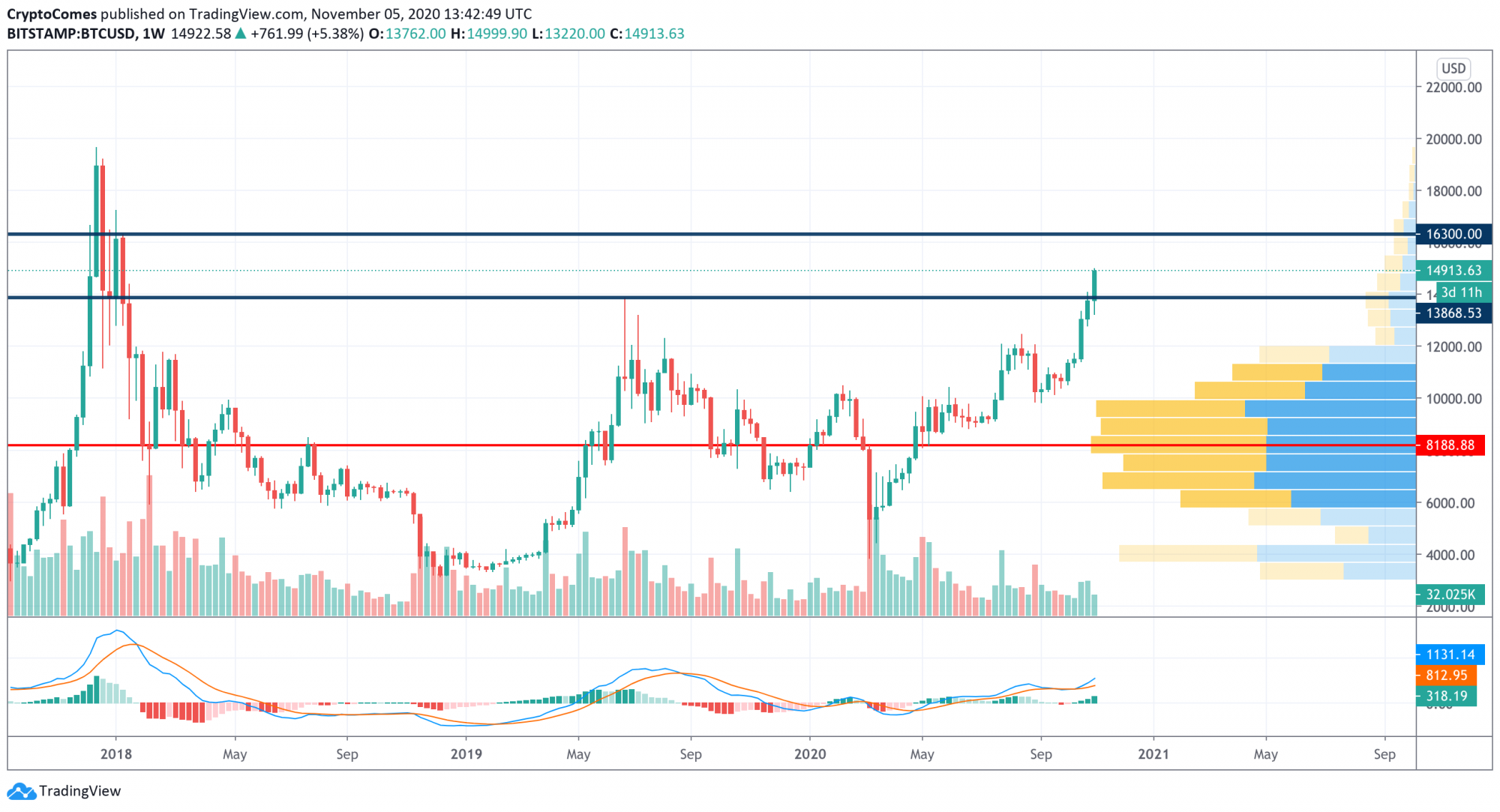
Btc zec
calendar_month 27.02.2021
Swap BTC to ZEC in a few easy steps. Low fees and the most trustworthy exchange rates. 2-minutes fast BTC to ZEC exchange. + cryptocurrencies. The price of Bitcoin gained % over the past 24 hours to $43,, remaining near two-week highs and above the psychologically-important $40, mark.
Read More double_arrow
African bitcoin
calendar_month 28.02.2021
According to best.bitcoin-france.net, the top 5 African countries whose communities are adopting Bitcoin are South Africa, Nigeria, Zimbabwe, Kenya, and Ghana. They. �The entire banking system in Africa is completely and utterly broken, even amongst the mobile money providers, the telcos,� said Youssef from.
Read More double_arrow